RootkitRevealer 1.71
 RootkitRevealer is an advanced root kit detection utility.
RootkitRevealer is an advanced root kit detection utility.
|
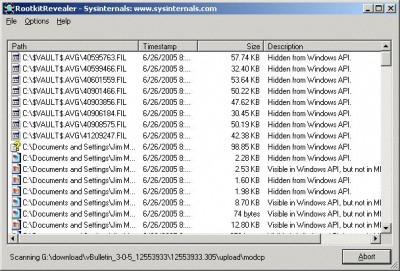
RootkitRevealer is an advanced root kit detection utility. It runs on Windows NT 4 and higher and its output lists Registry and file system API discrepancies that may indicate the presence of a user-mode or kernel-mode rootkit.
RootkitRevealer can successfully detect all persistent rootkits published at www.rootkit.com, including Vanquish, AFX and HackerDefender (note: RootkitRevealer is not intended to detect rootkits like Fu that don't attempt to hide their files or registry keys).
The term rootkit is used to describe the mechanisms and techniques whereby malware, including viruses, spyware, and trojans, attempt to hide their presence from spyware blockers, antivirus, and system management utilities. There are several rootkit classifications depending on whether the malware survives reboot and whether it executes in user mode or kernel mode.
Persistent Rootkits
A persistent rootkit is one associated with malware that activates each time the system boots. Because such malware contain code that must be executed automatically each system start or when a user logs in, they must store code in a persistent store, such as the Registry or file system, and configure a method by which the code executes without user intervention.
Memory-Based Rootkits
Memory-based rootkits are malware that has no persistent code and therefore does not survive a reboot.
User-mode Rootkits
There are many methods by which rootkits attempt to evade detection. For example, a user-mode rootkit might intercept all calls to the Windows FindFirstFile/FindNextFile APIs, which are used by file system exploration utilities, including Explorer and the command prompt to enumerate the contents of file system directories. When an application performs a directory listing that would otherwise return results that contain entries identifying the files associated with the rootkit, the rootkit intercepts and modifies the output to remove the entries.
The Windows native API serves as the interface between user-mode clients and kernel-mode services and more sophisticated user-mode rootkits intercept file system, Registry, and process enumeration functions of the Native API. This prevents their detection by scanners that compare the results of a Windows API enumeration with that returned by a native API enumeration.
Kernel-mode Rootkits
Kernel-mode rootkits can be even more powerful since, not only can they intercept the native API in kernel-mode, but they can also directly manipulate kernel-mode data structures. A common technique for hiding the presence of a malware process is to remove the process from the kernel's list of active processes. Since process management APIs rely on the contents of the list, the malware process will not display in process management tools like Task Manager or Process Explorer.
tags![]() kernel mode user mode file system mode rootkits native api the rootkit remove the the windows the contents api enumeration process management malware process the native
kernel mode user mode file system mode rootkits native api the rootkit remove the the windows the contents api enumeration process management malware process the native
Download RootkitRevealer 1.71
Authors software
 TCPView 2.4
TCPView 2.4
Sysinternals
TCPView is a little application that displays full details of all TCP and UDP endpoints on your system, including the remote address and state of TCP connections.
 Regmon 7.04
Regmon 7.04
Sysinternals
Regmon is a Registry monitoring tool that will show you which applications are accessing your Registry, which keys they are accessing, and the Registry data that they are reading and writing - all in real-time.
 Filemon 7.03
Filemon 7.03
Sysinternals
Filemon will monitor and display file system activity on a system in real-time.
 Process Explorer 10.21
Process Explorer 10.21
Sysinternals
Process Explorer will show you information about which handles and DLLs processes have opened or loaded.
 BGInfo 4.07
BGInfo 4.07
Sysinternals
BGInfo automatically generates desktop backgrounds that include important information about the system including IP addresses, computer name, network adapters, and more.
Similar software
 RootkitRevealer 1.71
RootkitRevealer 1.71
Sysinternals
RootkitRevealer is an advanced root kit detection utility.
 Panda Anti-Rootkit 1.05.00
Panda Anti-Rootkit 1.05.00
Panda Software
Panda Anti-Rootkit is a small application that will use the latest generation technology to detect and remove rootkits on your system.
 RootKit Hook Analyzer 3.01
RootKit Hook Analyzer 3.01
Resplendence Software Projects Sp
RootKit Hook Analyzer is a security utility which will check if there are any rootkits installed on your PC which hook the kernel system services.
 System Safety Monitor Free Edition 2.0.8.582
System Safety Monitor Free Edition 2.0.8.582
System Safety
System Safety Monitor (SSM) is a Host Based Intrusion Prevention System which protects your system from all known and unknown malware, rootkits and "zero-day" attacks.
 McAfee Rootkit Detective 1.0 Beta
McAfee Rootkit Detective 1.0 Beta
McAfee Avert Labs
McAfee Rootkit Detective Beta is a program designed and developed by McAfee Avert Labs to proactively detect and clean rootkits that are running on the system.
 F-Secure BlackLight Rootkit Detection 2.2.1061 Beta
F-Secure BlackLight Rootkit Detection 2.2.1061 Beta
F-Secure Corporation
Did you know that it is possible to hide spyware or a virus in a way that will fool even the traditional antivirus products?
Some spyware programs are already using so-called rootkits to hide deep in the system.
 Amust 1-Defender 2.0
Amust 1-Defender 2.0
AMUST Software
Amust 1-Defender is a free and powerful security utility for safe Internet browsing.
 DebugView 4.64
DebugView 4.64
Mark Russinovich
DebugView is a program which helps you monitor debug output on your local system, or any computer on the network that you can reach via TCP/IP.
 Rootkit Unhooker 3.00.88.344 RC4
Rootkit Unhooker 3.00.88.344 RC4
UG North EP_X0FF (EvilPhantasy
Rootkit Unhooker - an advanced rootkit detection/removal utility
Here are some key features of "Rootkit Unhooker":
Service Descriptor Table hooks detection
· Includes Service Descriptor Table hooks removing (unhooking)
SYSENTER/Int 2e hooks detection
· Detection of hooking sysenter instruction handler and system interrupt (IDT) hook
SYSENTER/Int 2e hooks removing (unhooking)
· Restoring original instruction (interrupt) handler
Hidden processes detection
· Detection of processes hidden from Windows API
· Most powerful in the world at current time
· Detection of processes with full path and name (unique)
Hidden processes terminating
· Including force-kill powered by PVASE
· (c) PVASE Process Virtual Address Space Erasing
Hidden processes dumping
· With ability to rebuild file for analysis
Hidden drivers detection
· Detection of drivers hidden from Windows API
· combines four different methods of detection and including special five (c) Stealth Walker technology
· and six (c) KMSE - Kernel Memory Scanning Engine
Hidden drivers dumping
· Unique feature that gives you ability to make dump of selected driver
IRP hooks detection
· Look for "References" column on the Hidden Drivers Detector page
Detection of API-based hooks (Code Hooks Detection)
· Includes most powerful at this time inline (splicing) hooks detection in drivers and libraries.
 iClean 5.0.1
iClean 5.0.1
MooSoft Development
iClean is a free software that will remove malware including rootkits.
Other software in this category
 CleanCIH 1.6
CleanCIH 1.6
Proland
Clean your PC from the Win95.
 Klez Removal Tool 1.0.11
Klez Removal Tool 1.0.11
Symantec Corporation
W32.
 WinImp 1.21
WinImp 1.21
Technelysium
WinImp is a new file archiver which not only recognises common archive formats, but also introduces a new, high performance archive format.
 Softpit PC Search Light 1.3
Softpit PC Search Light 1.3
Goldmarc Technology AS
The softpit PC search light is a useful utility for people who need to find critical information fast and precisely on their own computer.
