brute freeware downloads
Search results for «brute»:
 MD5 Brute Force Tool 1.0
MD5 Brute Force Tool 1.0
… by attempting to brutefoce them. This program will attempt to brute force the given md5 hash. The user can also specify the characters to use then bruteforcing.…
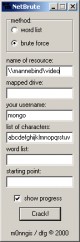 Network Share Brute Forcer 3.1
Network Share Brute Forcer 3.1
… Network Share brute Forcer will try and gain access to shared folders on your
network using one of the following two methods:
brute force attack
Dictionary attack…
 Extended Password Generator 1.5.1.628
Extended Password Generator 1.5.1.628
… EPG (Extended Password Generator) is the tool-at-hand of any system administrator to generate pronounceable and random passwords, secured against brute-force dictionary attacks.…
 dsCrypt 1.10
dsCrypt 1.10
… l implementation, performance and safety measures. dsCrypt uses an advanced encryption algorithm and offers unique options for enhanced security.
Features:
extensively tested and widely accepted algorithm
bruteHalt and exceptional resistance to brute-force password search
inherent resistance t…
.jpg) Brute Force Uninstaller (BFU) 1.0.9
Brute Force Uninstaller (BFU) 1.0.9
… lude unloading the shell (i.e. killing the Explorer.exe process), pausing between commands (or all commands) and setting a minimum required version number for BFU itself to be able to run the script. BFU itself does not store anything on the system a…
 BackupHDDVD 1.00
BackupHDDVD 1.00
… timate key.
The challenge is getting that key. You may recall that the first DVD rip software used a player key extracted from the Xing DVD player software - a key that was later removed by the CSS licensing committee.
Then came rippers that brute-forced a valid key (VobDec being the first o…
 XMLFoundation 1.0
XMLFoundation 1.0
… open source. - and it only gets better from here.
The Need for Objects from XML
The purpose of the XMLFoundation is to obtain data marked up in XML creates the need for Application Layer tools to easily and efficiently work with XML data. The brute force approach is to parse the XML into a tr…
 TigerCrypt 3.2
TigerCrypt 3.2
… bit AES. The encrypted data is indistinguishable from random data.
The password used for decryption cannot be verified. Whatever file is used for decryption, and whatever password is used, TigerCrypt always produces an output file. This makes a brute force attack almost impossible.
Open fil…
 PassPack 1.01
PassPack 1.01
… tial information. It features exceptional resistance to brute-force password search attacks. PassPack offers both import and export of unencrypted data.…
 Cain & Abel 4.8
Cain & Abel 4.8
… e encrypted protocols such as SSH-1 and HTTPS, and contains filters to capture credentials from a wide range of authentication mechanisms.
The new version also ships routing protocols authentication monitors and routes extractors, dictionary and brute-force crackers for all common hashing algori…
Related: