Harden-It 1.2
 Harden-It is a new lightweight software release from YASC .
Harden-It is a new lightweight software release from YASC .
|
Harden-It is a new lightweight software release from YASC .ltd and Zoller Thierry. Harden-it was created to harden your Windows installation against many attacks.
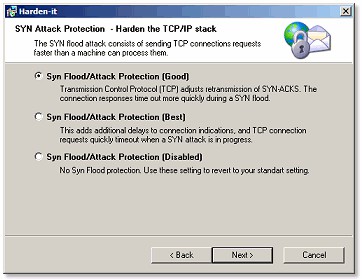
By hardening the IP stack your Network can sustain or completely twarth various sophisticated network attacks. By hardening your Local System lots of current malware, spyware, worm infection are completely blocked, proactively harden your system even against future uknown attacks.
Short Features:
Harden-It™ is intended for the network/server administrator or the professional internet user. You should not use this tool if you are a novice.
Features:
tags![]() how many free connections determines how specifies the syn rcvd the server shut down many times fragmented packets rcvd state computer browser harden your the network
how many free connections determines how specifies the syn rcvd the server shut down many times fragmented packets rcvd state computer browser harden your the network
Download Harden-It 1.2
Authors software
 Harden-It 1.2
Harden-It 1.2
YASC .ltd
Harden-It is a new lightweight software release from YASC .
Similar software
 Harden-It 1.2
Harden-It 1.2
YASC .ltd
Harden-It is a new lightweight software release from YASC .
 RemoteNetstat 1.3.4
RemoteNetstat 1.3.4
Nsasoft llc
Remote Network Statistics will display remote network computer IP, ICMP, TCP, UDP and Server statistics, shows the details about IP datagrams including forwarding enabled-disabled state, default time to live, the number of received datagrams, datagrams with address, protocol errors, header, forwarded datagrams, incoming datagrams that have been discarded, sent datagrams, delivered datagrams, routing datagrams that have been discarded, datagrams withought routing, interfaces, local host Ip address, TCP segments including timeout algorithm, minimum and maximum timeouts in milliseconds, the number of maximum connections, opened active and passive connections, failed connections, reset connections, currently established connections, received segments, sent segments, retransmitted segments, received errors, segments, which have been sent with reset flag, cumulative connections, details about UDP datagrams the number of received datagrams, datagrams without port, datagrams with errors, sent datagrams, listening connections, ICMP messages in incoming and outgoing states including the number of messages, errors, unreachable messages, TTL exceeded messages, messages with parameter problems, source quench messages, redirected messages, echo messages, echo replies, time stamp replies, address mask messages, address mask replies,etc.
 PingIt 2.0
PingIt 2.0
Desktop Software
The Program is a free program and intended for monitoring speed of your internet connections or monitoring of speed to certain IP-address.
 Bandwidth Management and Firewall 1.1.0
Bandwidth Management and Firewall 1.1.0
softinengines.com
Bandwidth Management and Firewall will allow to limit bandwidth for some computer or group of computers comunicating from/to internet or to limit bandwidth for some network service.
 Incoming Packet Monitor 0.5
Incoming Packet Monitor 0.5
Kushinara
Incoming Packet Monitor is a packet monitor designed to monitor SYN packets.
 AS3 Personal Firewall 1.6
AS3 Personal Firewall 1.6
AS3 Soft4U
AS3 Personal Firewall is device designed to prevent outsiders from accessing your network.
 fileXfer 1.5
fileXfer 1.5
United Business Technologies
fileXfer is a useful application which allows remote machine access for: Files, Registry, Processes, and Services.
 ZedMon 3.24
ZedMon 3.24
Toucan IT
ZedMon is a NetWare server monitoring tool that provides network administrators with at-a-glance information on user activity, network address, login time and protocol preference, as well as server utilization and open file information.
 IP Sniffer 1.91.5.0
IP Sniffer 1.91.5.0
Erwan L.
IP sniffer is a protocol analyzer, that will use the XP/2K Raw Socket features.
 VisualSniffer 2.0
VisualSniffer 2.0
BVTech Inc
VisualSniffer is a powerful packet capture tool and protocol analyzer (ip sniffer or packet sniffer) for Windows system.
Other software in this category
 Folder Size Shell Extension 3.2
Folder Size Shell Extension 3.2
Space Dolphin
Folder Size Shell Extension is a handy shell extension that adds a new tab to the Properties dialog that displays a folder`s or drive`s size.
 MouseCam 1.0
MouseCam 1.0
CamTech
MouseCam is a free little tool that zooms everything your cursor is over up to 20 times its normal size.
 Microsoft Windows XP Plus! Service Pack 1
Microsoft Windows XP Plus! Service Pack 1
Microsoft Corp.
Microsoft has released an update for its addon utility: Microsoft Plus! designed for the Windows XP operating system.
 ServiceManager 1.00
ServiceManager 1.00
L5 Software Group, LLC
ServiceManager is an application designed to allow System Administrators, Developers and Power Users an easy means to view, modify or remove services and their information.
 Command Finder 1.0
Command Finder 1.0
UCG Media
UCG Command Finder was created as a compliment for the Universal Command Guide to make it even easier, when you need a command, to find it.